Wyatt LeVine
-
Posted: July 23, 2024Read more »
In the security industry, staying ahead of the professional curve is not just beneficial—it’s essential. While binge-watching the latest series on Netflix can be a great way to relax, investing time in professional development can yield substantial returns. SecurityCEU.com’s Library Subscription offers an unparalleled opportunity for security professionals to enhance their skills, stay compliant, and advance their careers. Here’s why you should consider making the switch.
How the SecurityCEU.com Library Subscription Works
The SecurityCEU.com Library Subscription provides 12 months of unlimited access to an extensive catalog of CEU-approved courses. For a single, low fee, subscribers gain entry to a comprehensive range of training materials designed by industry experts. Whether you’re a seasoned professional or just starting out, this subscription caters to all levels of expertise and covers a broad
-
Posted: June 20, 2024Read more »
The security industry is experiencing explosive growth. As homes and businesses invest in advanced security systems, the demand for qualified professionals is skyrocketing. However, with great opportunity comes great responsibility. Security dealers and integrators play a critical role in safeguarding lives and property. This responsibility hinges on maintaining proper licensing and adhering to a complex web of regulations. Let's delve into why compliance should be a top concern for your security business and how Obsequio can be your ultimate solution.
The Compliance Tightrope: A Balancing Act for Security Businesses
Across 44 states and the District of Columbia, security professionals navigate a labyrinth of licensing requirements. These regulations vary by location and can encompass installation, maintenance, sales, support, and monitoring of security systems. Failing to comply can lead to severe
-
Posted: June 19, 2024Read more »
At CMOOR, we're dedicated to providing top-notch security industry education. SecurityCEU.com, one of our divisions, offers industry-leading training specifically designed for security professionals. Our commitment goes beyond just courses – we provide the tools and resources you need to succeed in the ever-evolving field of security.
Why Choose SecurityCEU.com for IP Video Training?
- Industry Standard Education: We set the bar high for security and systems education. Our instructors are experts who understand the challenges faced by security professionals today.
- Comprehensive IP Video Training Bundle: Our IP Video Training Bundle is a one-stop shop for everything you need to know about IP video surveillance systems. Whether you're new to
-
Posted: May 16, 2024Read more »
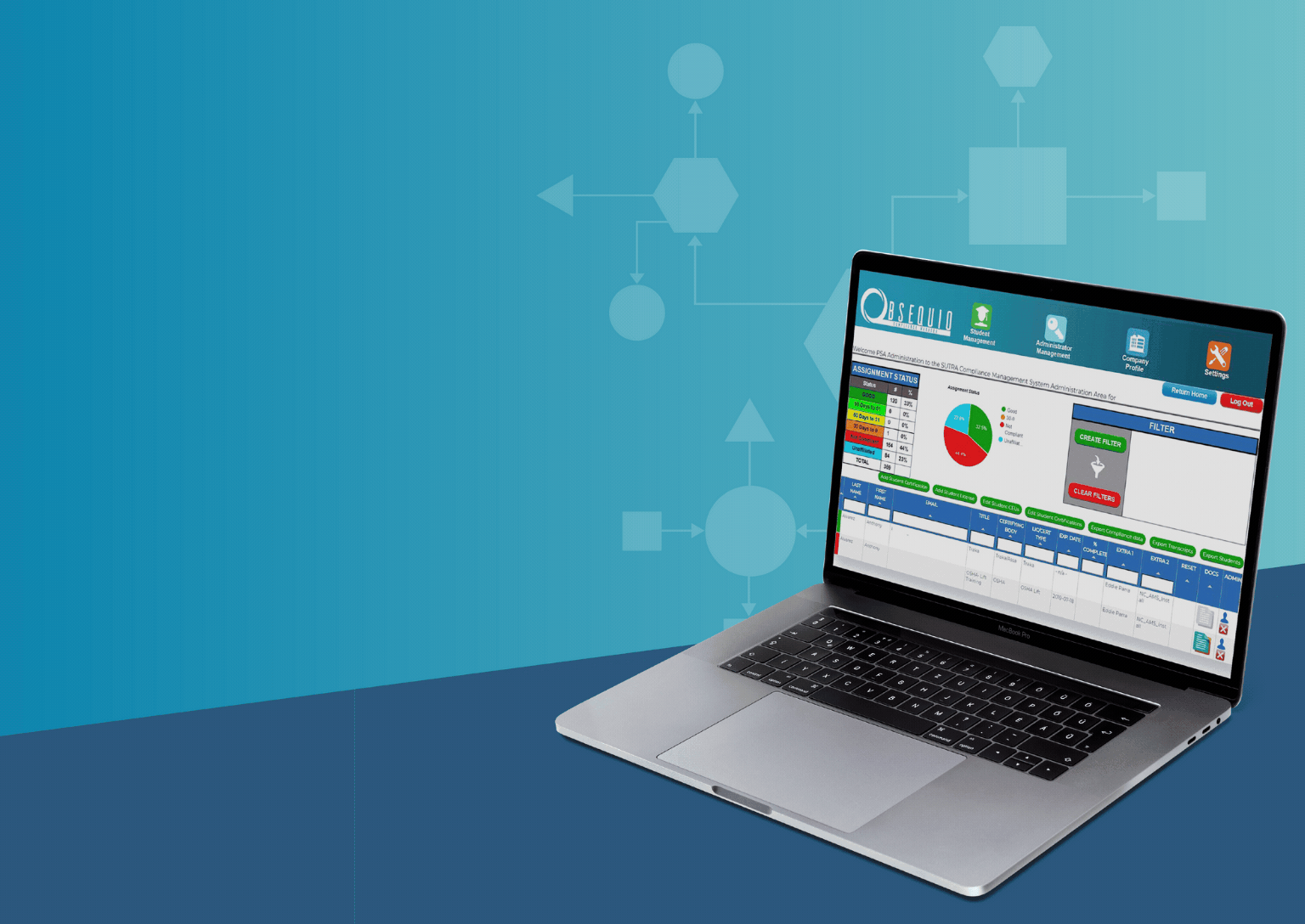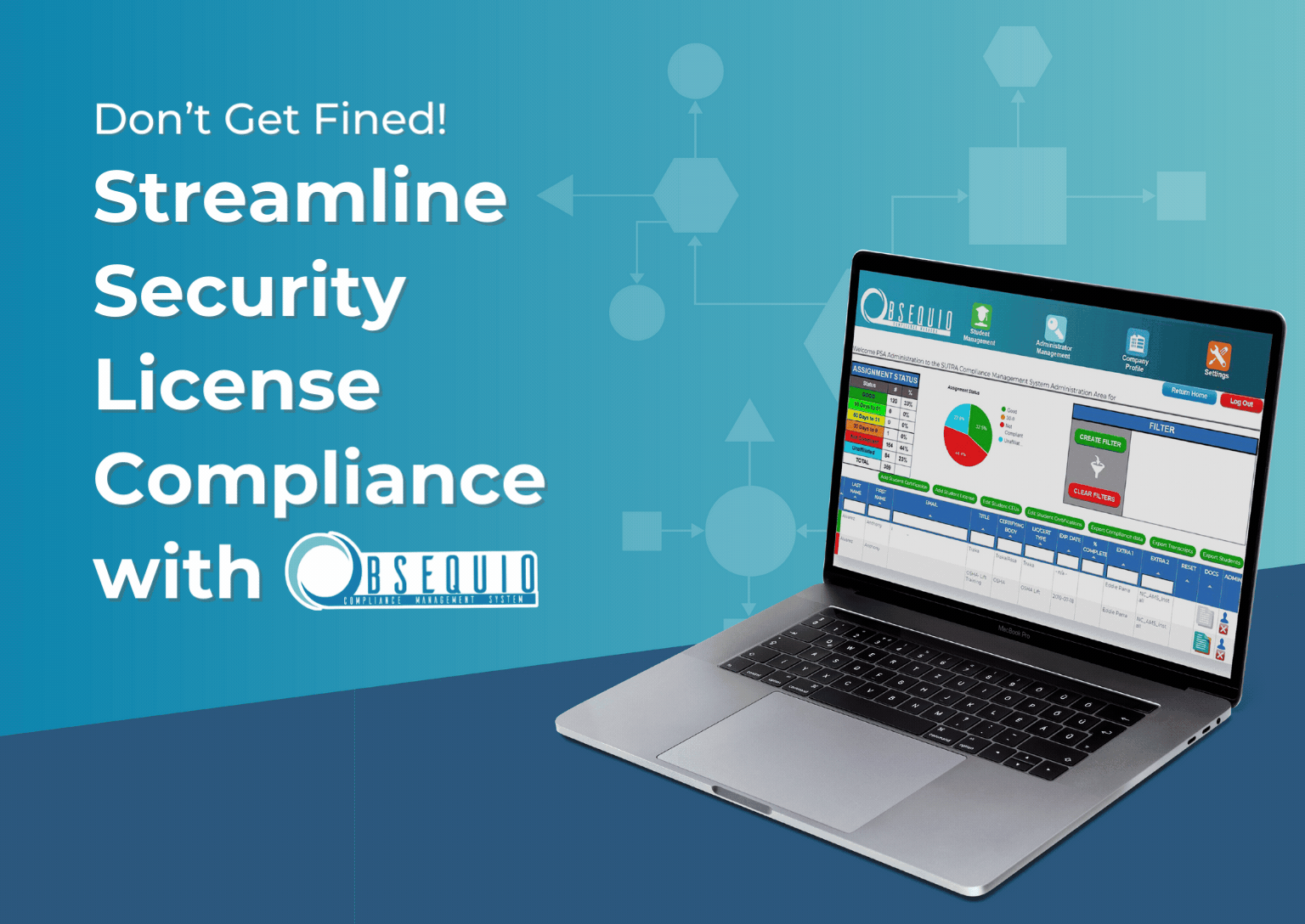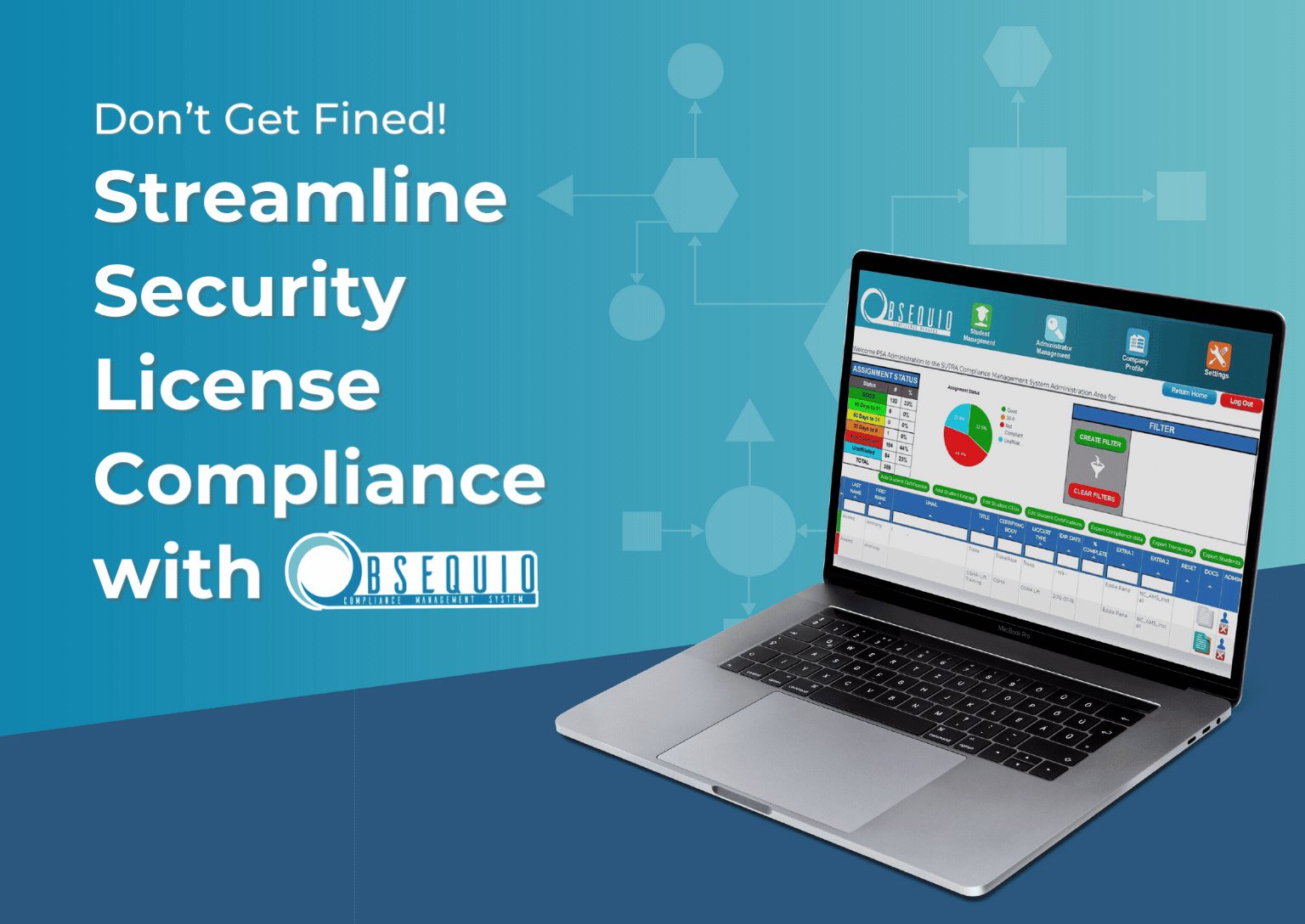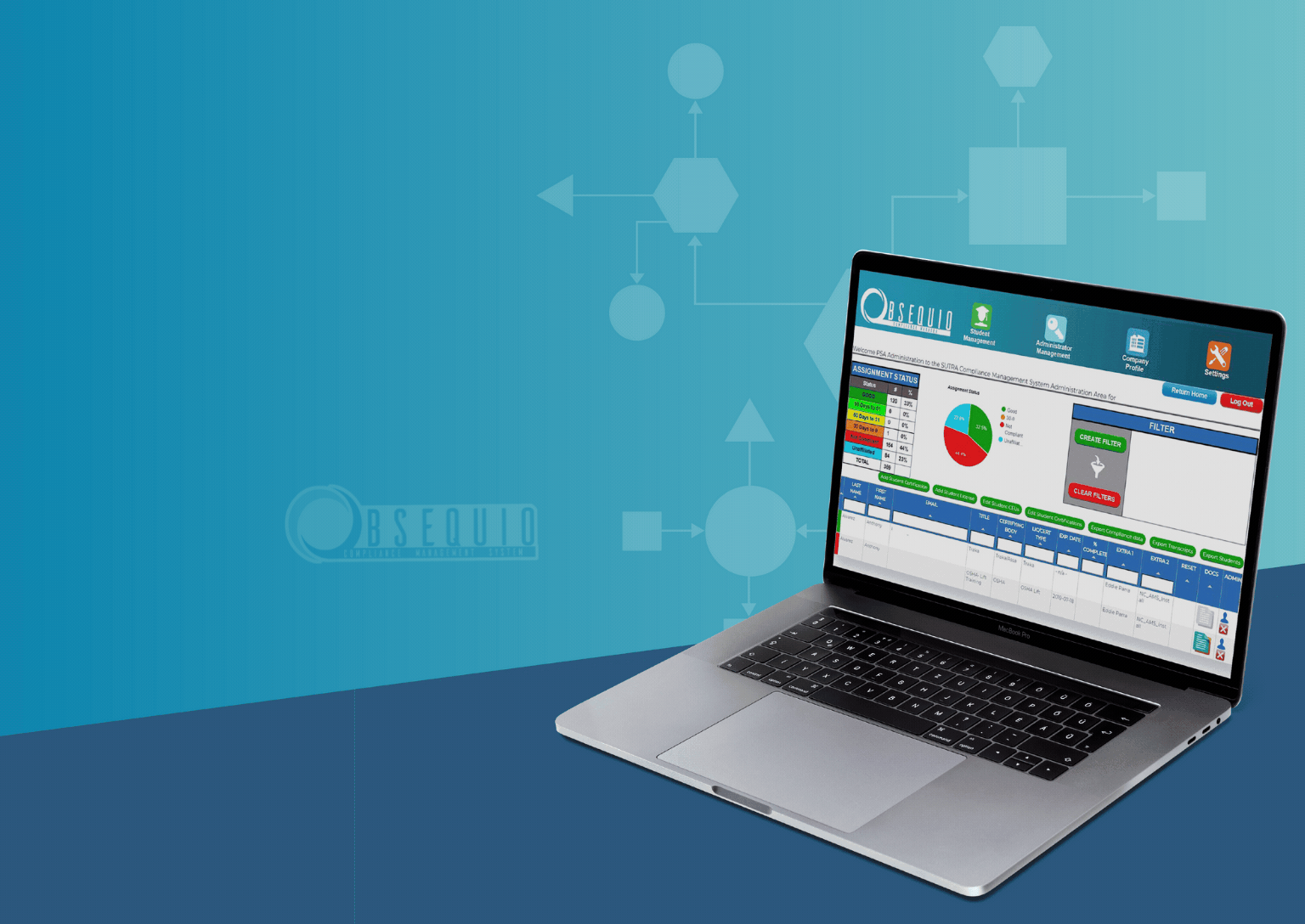
Top Compliance Management Nightmares Solved Obsequio Compliance Management
The security industry safeguards lives and property. But behind the scenes, security professionals face a constant challenge: navigating the labyrinth of compliance regulations. A complex web of licenses, renewals, and ever-changing legal requirements can consume valuable time and resources, hindering operational efficiency and growth.
Introducing Obsequio Compliance Management: Your Key Through the Maze
Obsequio Compliance Management emerges as your guiding light in the compliance labyrinth. This cloud-based software streamlines the entire licensing renewal process, empowering your security business to thrive in a highly regulated environment. Here's how Obsequio tackles the most critical challenges you face:
- Eliminate Paperwork Chaos:
-
Posted: May 09, 2024Read more »
Level Up Your Security Expertise with SecurityCEU's IP Video Training Bundle
The security industry is constantly evolving, and staying ahead of the curve requires ongoing education and training. SecurityCEU.com's comprehensive IP Video Training Bundle equips security professionals with the knowledge and skills they need to thrive in today's technology-driven landscape.
Why Choose SecurityCEU.com's IP Video Training Bundle?
- Developed by Industry Experts: The curriculum is designed by security professionals who understand the real-world challenges you face.
- In-Depth Coverage: The bundle delves into a wide range of topics, from networking fundamentals to video analytics, ensuring you have a well-rounded understanding of IP video systems.
-
Posted: April 18, 2024Read more »
5 Reasons SecurityCEU.com is Your One-Stop Shop for Security Training
In today's ever-evolving security landscape, staying ahead of the curve is crucial. Security professionals like yourself need access to high-quality, compliant training that fits your busy schedule and learning style. That's where SecurityCEU.com comes in.
- Unmatched Content Breadth and Depth:SecurityCEU.com boasts an industry-leading library with over 165 hours of security, fire, and life safety CEU content. This isn't just generic training – it's developed by security professionals for security professionals. Whether you're a seasoned veteran or just starting out, you'll find courses that address your specific needs. From mastering the intricacies of IP video surveillance to staying compliant with the latest fire alarm standards, SecurityCEU.com has you covered.
- Flexible Learning Options for Busy Professionals:
-
Posted: April 18, 2024Read more »
5 Ways Obsequio Makes Security License Renewal a Forget-About-It Breeze
Staying compliant with security license renewals in today's complex regulatory landscape can feel like walking a tightrope – one missed deadline or misplaced document could lead to hefty fines, business disruptions, and even legal repercussions. But what if there was a way to eliminate the stress and streamline the entire process?
Obsequio is your secret weapon for transforming security license renewal from a bureaucratic nightmare into a forget-about-it breeze. Here's how:
- Automated Renewal Guardian: Ditch the spreadsheets and sticky notes. Obsequio automates the entire renewal process, sending customizable email alerts 90, 60, and 30 days before a license expires. This ensures your team has ample time to renew and eliminates the risk of accidental lapses that
-
Posted: March 11, 2024Read more »
Streamlining Security Compliance: A Deep Dive into Obsequio’s Key Features
In the volumes of regulations governing the security industry, maintaining compliance through proper licensing and certification is not just a requirement; it's a cornerstone of operational integrity and professionalism. Across 44 states and the District of Columbia, security professionals face a daunting task: navigating the complex, often murky waters of state and local regulations to ensure every technician, installer, and support staff member holds a valid license. The risks of non-compliance are severe, ranging from hefty fines to business shutdowns and, in some scenarios, jail time.
Fortunately, there is a tool designed specifically for the security industry to help manage this burden-- Obsequio Compliance Management System.
Obsequio isn't just another compliance tool; it's a comprehensive compliance management system that revolutionizes how licensing and certification renewals
-
Posted: March 11, 2024Read more »
SecurityCEU.com’s Subscription Model: Revolutionizing Professional Development in the Security Industry:
Success in the electronic security industry requires a commitment to continuous learning and professional development. This can be a difficult process without the right tools, platform, and support.
SecurityCEU.com, powered by The CMOOR Group, has revolutionized the approach to continuing education for security professionals with its innovative subscription model.
This model not only provides unmatched flexibility and value but also ensures that learners have access to a comprehensive range of courses tailored to their needs.
Unrivaled Flexibility for Continuous Learning
The heart of SecurityCEU.com’s offering is its Library Subscription model, which allows learners to access an entire catalog of CEU-approved courses for a single, low fee. This approach is designed to cater to the varied
-
Posted: February 16, 2024Read more »
5 Common Compliance Pitfalls in the Security Industry and How to Avoid Them
In the tightly regulated world of the security industry, staying compliant isn't just about ticking boxes; it's about safeguarding your business's future. With regulations spanning across states and even city levels, it's easy to stumble into pitfalls that can lead to hefty fines, operational disruptions, or worse.
Here, we explore five common compliance mistakes in the security industry and provide practical tips to help you navigate these challenges effectively.
1. Overlooking Local and State Regulations
Many security businesses understand the need for federal compliance but often underestimate the complexity of state and local regulations. This oversight can be costly.
How to Avoid It: